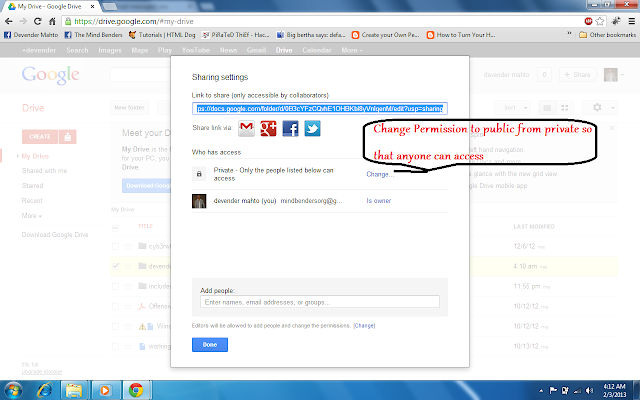
I was just wondering around to have a look on the most famous conferences for Hackers and when i got to know about so many people and groups running these motivating communities, I set up myself for listing nearly all HACKERS conferences happening here and there. I might have missed some conferences and if yours is not on the list, I am sorry about it. Please let me know about yours so that I can include it too.
1. DefCon

DEF CON holds the title of world's largest annual hacker convention. It was first held in Las Vegas, NV in 1993 and continues today. Attendees include a wide range of personalities interested in the hacking world, general interest groups, federal government employees, lawyers, and hackers. Its focus ranges from computer and hacking related subjects, social events, and contests such as creating the longest Wi-Fi connection to cracking computer systems to non-related computer contests. The best known contest is Capture the Flag where teams of hackers attempt to attack and defend computers and networks.
2. Black Hat

The Black Hat Briefings is a computer security conference that brings together a variety of people interested in information security. Representatives of federal agencies and corporations attend along with hackers.
Black Hat is composed of two major sections, the Black Hat Briefings, and Black Hat Trainings. Training is offered by various Computer security vendors, in effort to keep the conference vendor-neutral. In the past, the conference has hosted the National Security Agency's Information Assurance Manager course, and various courses by Cisco Systems, Offensive Security, and others.
3. DerbyCon

At DerbyCon security professionals from all over the world come to hang out. Next DerbyCon 2.0 will is going to held this September 27-30th, 2012. They had pulled in over as much as 1,100 people with an amazing speaker lineup and a family-like feel. Their basic goal is to keep it around the same size and maintain a close-knit conference where they can all come together to learn and share ideas.
4. NullCon
Null is an open source community full of Security Professionals who love to share their knowledge with means of various monthly meets, seminars and conferences. In India, they are the biggest Security community with chapters in 7 major cities. Nullcon Security Conferences is an Initiative by Null - The Open Source
Community. It Is Moreover is a unique platform for security companies/evangelists to showcase their research and technology. Nullcon hosts Prototype, Exhibition, Trainings, Free Workshops, null Job Fair at the conference.
5. ShmooCon

ShmooCon is an American hacker convention organized by The Shmoo Group. There are typically about 35 different talks and presentations, on a variety of subjects related to computer security and cyberculture.
6. OWASP

OWASP also conducts its annual international information security conference, and the last one was OWASP InfoSec India Conference 2012 - "India's Cyber Security Kumbh", which was held from August 24-25, 2012 in Delhi NCR, India.
OWASP events in India have become a distinguished platform to bring industry leaders, InfoSec professionals, developers, regulators and high-profile officials from defence and security establishments together from around the world.
7. ClubHack

They started in 2007 conducting and witnessing a lot of action with their aim of making the genera people including media and professionals more aware and serious about Security.
8. HITB
9. HOPE

HOPE (abbreviation of Hackers on Planet Earth) conference series is sponsored by the hacker magazine 2600: The Hacker Quarterly and typically held at "Hotel Pennsylvania", in Manhattan, New York City. Held biennially in the summer, there have been nine conferences to-date; the most recent occurring 13–15 July 2012.
The "Last HOPE" took place 18–20 July 2008 at the Hotel Pennsylvania.The name referred to the expectation that this would be the final H.O.P.E. conference due to the scheduled demolition of its venue, the Hotel Pennsylvania. The "Next HOPE" was scheduled for Summer 2010. At the closing ceremony it was revealed that the use of the word "last" could also refer to the previous event, or one that had ended (referring to The Last HOPE itself).
10. Malcon

MALCON is an annual information security conference focusing exclusively on malware. They aims for bringing together the Malware and InfoSec researchers from the world to share key research insights into building and containment of the next generation malwares. The first MalCon conference took place in December 2010 at Mumbai and Pune, India. They have their audience in Security Professionals, Government Employees, lawyers, journaalists and hackers with interest in malwarism.
11. SummerCon

Summercon is one of the oldest hacker conventions, and the longest running such conference in America. It helped set a precedent for more modern "cons" such as H.O.P.E. and DEF CON, although it has remained smaller and more personal. Summercon has been hosted in cities such as Pittsburgh, St. Louis, Atlanta, Washington, D.C., Austin, Las Vegas, and Amsterdam. Originally run by Phrack, the underground ezine, and held annually in St. Louis, the organizational responsibilities of running Summercon were transferred to clovis in 1998 and the convention took place in Atlanta, dubbed 'Summercon X'.
12. SourceConference

SOURCE Conference is the world's premier conference and training event to focus on bringing together the business and technical communities. At SOURCE, technical experts publish advanced research and network for job opportunities, while executives keep up with the technology that shapes their important decisions. Both leave SOURCE with an understanding of each other's perspectives on the critical security problems that face the world.

A complete and comprehensive conference workshop that educates and equips its participants with the in-depth knowledge of understanding vulnerabilities and countermeasures to overcome the security infringements present today.This conference is a global series of Computer and Information Security conferences presented by EC-Council. The objective of the Hacker Halted conferences is to raise international awareness towards increased education and ethics in IT Security. The event is currently in its 14th year. Also present at Hacker Halted is EC-Council's H@cker Halted | Academy, trainings and workshops led by EC-Council instructors and trainers.
14. PhreakNIC

PhreakNIC is an annual hacker and technology convention held in Nashville, Tennessee. It is organized by the Nashville 2600 Organization and draws upon resources from SouthEastern 2600 (se2600).
PhreakNIC continues to be a long-time favorite among hackers, security experts and technology enthusiasts. PhreakNIC currently holds claim as the oldest regional hacker con and is one of the few hacker cons run by a tax-free charity.
PhreakNIC is attended by hackers and other technology enthusiasts from across the United States, although, as a regional conference, most of its attendees come from a two-state radius around Tennessee, including groups from Missouri, Ohio, Washington, DC, Georgia, Kentucky, and Alabama.
15. KiwiCon

Kiwicon provides a venue for hackers and computer security professionals as well as other interested parties to get together and share knowledge, war stories and to consume a startling amount of beer. In the spirits of H.O.P.E. and DEFCON, Kiwicon intends to bring together the best and brightest from academia, the computer security industry, the hacker underground, those who manage critical infrastructure and law enforcement.
The conference format allows for talks of various lengths on a wide range of subjects of interest, informal discussions, socialising and competitions. In the past there has been free coffee, free breakfast, and always a healthy amount of free beer.
16. InfiltrateCon

Infilterate is the first depp technical conference by Immunity which focuses on entirely technical issues. This conference is more focused towards those who have their excellent minds always working in offensive security issues. No policy or high-level presentations, just hard-core thought provoking technical meat. World-renowned researchers focused on the latest technical issues will do the presentations – demonstrating techniques you can’t learn about anywhere else. In order to keep Infiltrate accessible, we are limiting attendance to 100 attendees.
17. SANS
SANS is the most trusted and by far the largest source for information security training in the world. They offer training through several delivery methods - live & virtual conferences, mentors, online, and onsite.
18. HackBattle

This time the Hack Battle is fully integrated in the TNW2012 Conference ending with the grand finale of the Hack Battle presentations on stage during the Conference.
The TNW Kings of Code Hack Battle brings world leading platforms (API's and SDK's) together with an exclusive international group of coders (frontend and backend developers and designers).
19. LayerOne

LayerOne is a computer security conference located in Anaheim, California. They have been eight years old in the market and they feature speakers from all across the globe. The topics these guys covers range from lockpicking and MPLS security to covert data gathering and HIPAA compliance. This is due to fact that the spekers here come from a diverse background and include a focus not just on the nuts and bolts of technology but the social impact as well.

The PacSec meeting provides an opportunity for foreign specialists to be exposed to Japanese innovation and markets and collaborate on practical solutions to computer security issues. In a relaxed setting with a mixture of material bilingually translated in both English and Japanese, the eminent technologists can socialize and attend training sessions.
The presenters are experienced security professionals at the vanguard of leading information security technology as well as experienced instructors who have prepared tutorials intended to help you stay abreast of the latest developments in this rapidly moving technological field. The best, and brightest, have assembled unique new material to help you maintain your technological leadership - which they will present at this conferences.
21. SecTor

SecTor was founded on a passion for security and it doesn’t take long to realize that security extends far beyond the bits and bytes. They assure to ensure that they will provide quality content – current information you can’t get anywhere else. The same rigor and dedication that their advisors apply to the selection of the technical content is also invested in selecting the management track session. Marketing fluff is not allowed or tolerated. Their conferences includes latest research, approaches, trends, Privacy and Compliance Issues, networking stuff, purist approach and experts from around the world.
22. NotaCon

NOTACON is an annual event that focuses on people who like to build, make, break and hack stuff. For many, it is a different kind of conference experience, while maintaining some familiar aspects of other hacker conferences. Showcasing: technologies, philosophy and creativity often overlooked at other events.
23. United Security Summit

The UNITED ("Using New Ideas to Empower Defenders") Security Summit is the venue for innovation and collaboration in the security community. At UNITED, security professionals engage in straight talk, share actionable advice and debate issues. This year's theme, "Truth, Lies & Decisions: moving forward in an insecure world," continues the tradition. They target their audience in IT Security directors, managers, architects, practitioners,Analysts, etc.
24. HacKid
HacKid is a new kind of conference focused on providing an interactive, hands-on experience for the entire family — kids aged 5-17 & their parents — in order to raise awareness, excitement and understanding of technology, gaming, mathematics, safety, privacy, networking, security and engineering and their impact on society and culture.
25. Athcon
AthCon is an annual, European two-day conference targeting particular areas of information security. It’s aim: to bring leading information security experts together. Attacking techniques of exploitation and various forms of penetration testing have become an important component of any organisation. This conference aims to provide a venue for understanding the ever evolving changes as well as new threats.
So for any instance you want to attend a conference, or speak something of your own stuffz, or play the CTF, look around these conferences and keep exploiting around.