Hi To All The
Requirements:-
1. Backtrack 5 or any Linux Distro Having msfencoders
2. your own virus/rat/keylogger engine mine is test1.exe
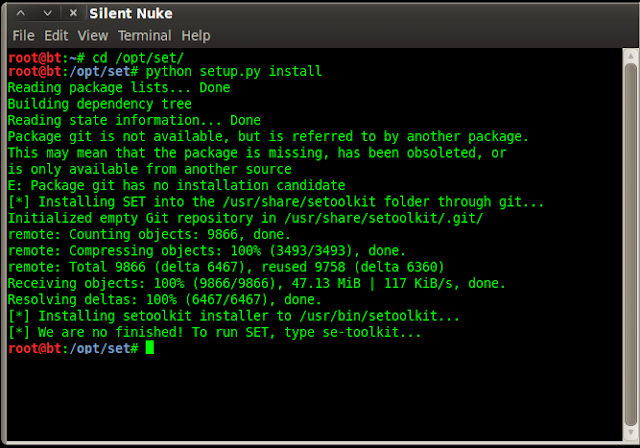
follow The commands shown in figure:-
perform all steps having root permission
Note:- click on image to see a bigger image
if You Have Any Query Write in Below Comments...
We Will Try To Figure out
Requirements:-
1. Backtrack 5 or any Linux Distro Having msfencoders
2. your own virus/rat/keylogger engine mine is test1.exe
follow The commands shown in figure:-
perform all steps having root permission
Note:- click on image to see a bigger image
if You Have Any Query Write in Below Comments...
We Will Try To Figure out